🔐 How to share Secrets via Vault (One-Time Secure Link)
Vault is a secure feature in AirMDR designed to streamline how secrets (like API keys, credentials, or tokens) are requested and handled for products.It allows security teams to securely collect sensitive data directly from clients without requiring login access, reducing operational friction while maintaining compliance and security standards.
AirMDR Vault ensures that your sensitive data is protected and only accessible by authorized team members.
📧 Step-by-Step: What You Need to Do
1
Check Your Email
-
You will receive an email from AirMDR system that looks like this:
Subject: Action Required: Provide Secret for <Name> Organisation
From: AirMDR Vault System <[email protected]>
Includes:- Required Secret name (e.g., “EDR API Key”)
- Secure link to upload secret
- Instructions or description (e.g., Message from requester: “Please provide the Login credentials to your Lorem Ipsum console so that we can monitor your dashboard as discussed in our weekly sync-up”)
2
Click the Secure Link
-
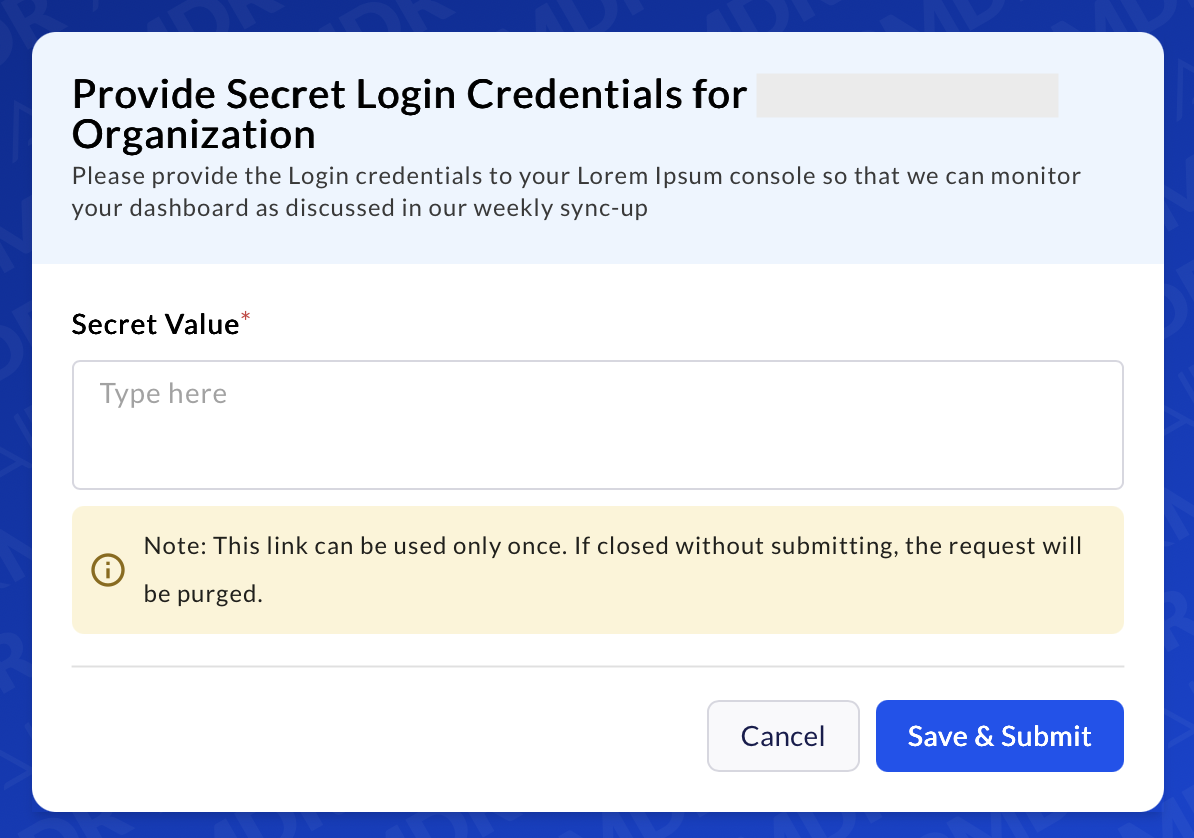
Click the “Provide Secret” button or link provided in the email.
 This link is secure, one-time use only, and expires at a pre-defined set time (e.g., 24 or 48 hours) by AirMDR.If the link has already been used or expired, you will see an error message.
This link is secure, one-time use only, and expires at a pre-defined set time (e.g., 24 or 48 hours) by AirMDR.If the link has already been used or expired, you will see an error message.
3
Paste the Secret
Once the page loads:
- You’ll see a secure input box labeled “Secret Value”.
- Paste the secret value.
-
Click “Save & Submit”.
🛡️ Compliance & Auditing
Vault logs captures all these to maintain transparency:- Who requested a secret
- Provided on (Date & Time)
- Who provided the secret
- When it was accessed or expired

