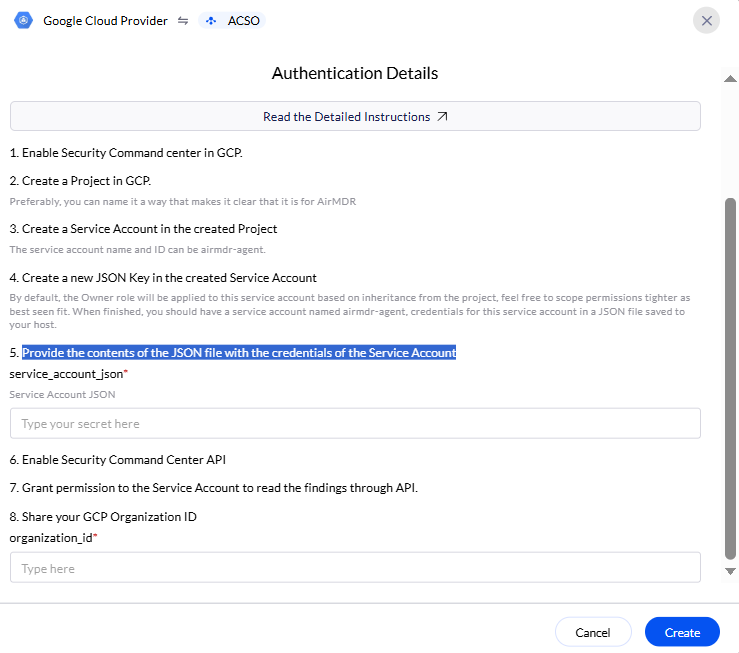
Pre-requisites
User Organization must define Owner or Security Admin role (
roles/owner or roles/securitycenter.admin) in your GCP organization.User must have Organization Admin permissions to enable services at the organization level.
Enable Security Command Center
Enabling Security Command Center will actively monitor your GCP environment for threats and vulnerabilities.1
Access GCC
- Log in to your Google Cloud Console.
- Click on the left navigation menu (hamburger icon).
-
Select the “Security” tab.
\
-
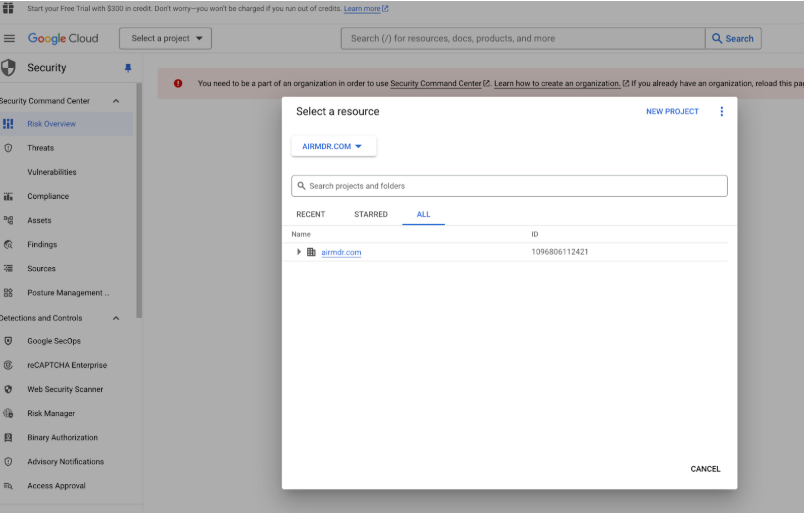
To select the organization where you want to enable SCC, click on Select a project > ALL.
Organization is displayed at the top-level and all the projects are indented
-
Copy the organization ID displayed next to the organization’s Name.\
2
Enable Security Command Center API
- In the Navigation menu, go to APIs & Services → Library.
- Search for Security Command Center API.
- Click Enable.
3
Select Service Tier
- Select your organization, and enter keyword “Security” in the search bar.
-
Select the Security Command Center.\
- Click on “GET THE SECURITY COMMAND CENTER”.
-
Select Service Tier, preferably Premium (Paid) for your organization.
SCC Editions: Standard vs. PremiumFeature Standard (Free) Premium (Paid) Security Health Analytics ✅ Basic ✅ Advanced Event Threat Detection ❌ No ✅ Yes Container & VM Threat Detection ❌ No ✅ Yes Continuous Compliance Monitoring ❌ No ✅ Yes Automated Security Insights ❌ No ✅ Yes - Click Next.
- On the next page, review the detection you want to enable.
4
Configure Security Sources
- Set Up Built-in Security Services
-
SCC integrates with:
- Security Health Analytics
- Event Threat Detection
- VM Threat Detection
- Container Threat Detection
- Configure these services based on your security requirements.
-
SCC integrates with:
- Enable Third-Party Integrations (Optional)
- Navigate to Integrations and configure security tools like SIEM, Threat Intelligence, etc.
- Click Next.
- On the next page, click Grant roles automatically to complete the setup.
You can view your findings in the findings tab on the left side.
Create a Service Account
1
Open Google Cloud Console
- Go to Google Cloud Console.
-
Select your project. For example: AirMDR
Project (Service account) is mandatory to enable API.
-
Create a project, if there is no existing
- Go to Google Cloud Console with the same credentials used to log in.
- Click Select a project → New Project.
- Enter:
- Project Name (e.g.,
AirMDR) - Organization (if applicable).
- Project Name (e.g.,
- Click Create.
2
Create a Service Account
- Go to Google Cloud Console.
- Select AirMDR project.
- Open APIs & Services → Go to Credentials→ Create Credentials → Click Service Accounts.
- Click Create Service Account.
-
Enter the required information:
- Service Account Name: (e.g.,
airmdr-agent) - Service Account ID : (e.g.,
airmdr-agent) - Click Create and Continue.
- Service Account Name: (e.g.,
-
Generate a Key File
- In the Service Accounts list, click on the created service account
- Go to Keys → Add Key → Create new key
- Choose JSON, then Create
-
A
.jsonkey file will be downloaded.
-
Assign IAM Roles
By default, the Owner role will be applied to this service account based on inheritance from the project
-
Add roles as required for Security Command Center:
- Security Admin (
roles/securitycenter.admin) → Allows managing SCC. - Viewer (
roles/viewer) → Grants read access. - Security Analyst (
roles/securitycenter.analyst) → (Optional) For security monitoring. - Pub/Sub Publisher (
roles/pubsub.publisher) → (Optional) For security alerts.
- Security Admin (
-
Click Continue → Done.
When finished, you should have a service account named airmdr-agent, credentials for this service account in a JSON file saved to your host.
-
Add roles as required for Security Command Center:
3
Enable Security Command Center API
- Go to Google Cloud Console.
- Select AirMDR project, go to APIs & Services → Enabled APIs & Services.
- Search for Security Command Center API from the Library page.
- Click Enable.
4
Assign the Required IAM Role
The Security Command Center Viewer role (
roles/securitycenter.viewer) allows the service account to read SCC findings.- Go to Google Cloud Console → Organization in the top left corner.
- Select AirMDR project.
- Go to IAM & Admin → VIEW BY PRINCIPALS → GRANT ACCESS.
\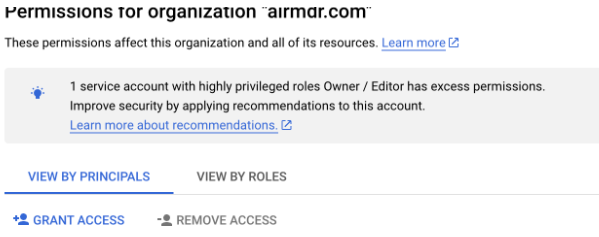
- Search and select
airmdr-agent. - Click Add.
or - Enter the client service account email (e.g.,
[email protected]). - Assign the role:
- Security Command Center Viewer (
roles/securitycenter.viewer)
- Security Command Center Viewer (
- Click Save.
5
Service Account
Email the service account
.json file and the Organization_ID to the AirMDR operations team mailto:[email protected] or self-configure in AirMDR Integrations Dashboard.Configure GCP Security Command Center API in AirMDR Integrations Dashboard
-
Navigate to AirMDR, provide the credentials and click Login.

-
Navigate to the AirMDR Integrations Dashboard in the left navigation pane and select Integrations.
\
-
Use the search option, enter the keyword “Google Cloud Provider”, select the Connections tab, and click the + Create icon.
\
-
Enter the generated organization ID, provide the contents of the JSON file with Service Account credentials in the Authentication Details field params, and click Create.
\